Credentials Management
Defining a Tenants Credentials per Category
Before you define credentials, we must first examine the concept of credentials in greater detail.
About Credentials
Credentials are the authentication methods used when connecting to the various devices that exist on the monitored network. Authentication methods vary depending on the type of device and therefore there are several predefined credential types to select from, such as Windows User/ Authenticated User/password, SNMP v1, 2 or 3, SSH, Telnet, and so on).
Credentials contain all the information needed to connect to and retrieve data from the data source, such as the DSN in ODBC connections, the port in SSH/Telnet connections, and so on.
Data sources can usually work with more than one type of credential. For example, a Linux CPU monitor can be given a user and a password and be told to connect using Telnet, or SSH. Or it may be given a public key and then use SS H's Public Key Infrastructure to login into the remote server. Groups of all the possible credential types for a monitor are called credential categories. In our example, it would be called Linux Operations and include Telnet, SSH with User/Password, and SSH with PKI. Note that another category exists, Linux Security, which contains exactly the same credential types. Credentials used for security monitors however usually have higher privileges than those used for operations, they are therefore separated so as to allow different defaults to be defined.
Credential categories are used only for convenience. This concept does not exist in ThinkServer and nothing prevents a credential from being used in any category which contains its type, or by a monitor that is said to use a different credential category.
Once a credential is defined as the default for a Tenant's given credential category, all monitors created for that category will use it if no other credential is assigned manually. Whenever a credential is created, it is checked whether it is compatible with a credential category with no defined default. If true, it will be assigned automatically. This means a default credential will always be defined as long as one valid credential exists.
Credential Categories
Credential categories are described in the table below:
| Credential Category | Description |
|---|---|
| User/Password | This credential only defines a user/password pair (without domain). But you can reuse the user/password combination. |
| Authenticated User / Password | Authenticated Users are all users who have been authenticated to the domain or a domain that is trusted by the computer domain. |
| Database DSN | Data Source Name (DSN) credentials are used by Open Database Connectivity (ODBC) to refer to the drive and other information that is required to access data stored in databases. This credential is defined by the name of the DSN and the User/Password credentials used to connect to the database. |
| FTP | Credentials of this category are used to discover and monitor various devices, like FTP servers. |
| iSeries | This credential category is used to access the iSeries machines that you will be monitoring. |
| JMX Digital Certificate | JMX Digital Certificate credentials are used to access Java Virtual Machines (JVMs). Digital certificates are defined by a Trust Store File and a Key. Both are encrypted using one of several available encryption algorithms. |
| Microsoft 365 | Microsoft 355 credentials are used to monitor Microsoft Office 365 assets. |
| Oracle TNS | Oracle TNS (Transparent Network Substrate) credentials are used to access Oracle networks. TNS provides a uniform application interface to enable network applications to access the underlying network protocols transparently. This credential is defined by the name of the TNS and the User/Password credentials used to connect to the database. |
| POP3 | Credentials you provide here will help find various network devices. |
| Proxy | This credential is used to act as a web proxy between Event Manager and Microsoft API. |
| SMTP | This credential category is used to access mail servers using an SMTP service. |
| SNMP Credential v1/v2 | Simple Network Management Protocol (SNMP) credentials are used to access devices on IP networks such as routers, switches, servers, etc. This credential is defined by its Community (community string). The SNMP community defines the relationship between an SNMP server system and the client systems, acting like a password to control the clients' access to the server. |
| SNMP Credential v3 | SNMP v3 does not employ community-based security (as used by SNMP v1 and v2). This credential is defined by its Authentication protocol, Privacy protocol, and Security. |
| SSH (Public Key) | SSH uses public-key cryptography to authenticate the remote computer and allow the remote computer to authenticate the user, if necessary. This credential requires a PKI file (defined by its path) and the port where the SSH server is listening (22 by default). |
| SSH (User / Password) | Secure Shell or SSH credentials are used primarily on Linux and Unix based systems to access shell accounts. This credential requires a valid user/password pair and the port where the SSH server is listening (22 by default). |
| Telnet (User / Password) | Telnet credentials are typically used to establish a connection to a Transmission Control Protocol (TCP) port number, where a Telnet server application (telnetd) is listening. This credential requires a valid user/password pair and the port where the Telnet service is listening (23 by default). |
| WebSphere MQ | Credentials of this category are used to find WebSphere MQ servers. Monitors for Message Queues and Channels can then be produced. |
| Windows User | Windows user credentials are used by the operating system and authenticated by the Local Security Authority (LSA). This credential is defined by the Windows Domain (or machine name, if a local user), user name, and password. |
Assigning Credentials
Once you’ve defined the basic properties of your Tenant, you can assign credentials to the Tenant’s credential categories.
- User/password
- Windows
- SNMP
This will be enough for Event Manager to find a good number of available devices on your network. Then, later, you can assign credentials in the remaining credential categories.
Go to configuration home and select Credentials Management. Tenants, with their credential categories appear at the left side of your browser.
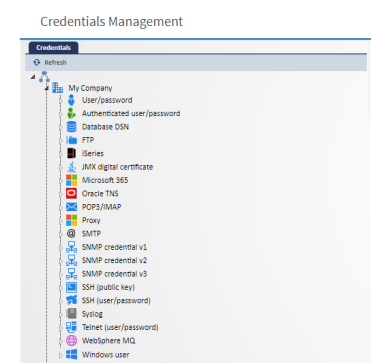
Refresh
Click the Refresh button to refresh the Credential Categories tree.
Copy
Click a credential and select the Copy button to create a copy of it. The copy appears under the same credential category for the same Tenant.
Edit
To edit an existing credential, expand its credential category and select the credential. An Editing Panel appears on the right. See Creating Credentials for a Credential Category for editing instructions
Click Save to save any changes you have made.
Creating Credentials for a Credential Category
To add a new credential to a credential category
- Click the arrow next to a credential category and select Add. A specific window named after the credential category appears. Each Credential Category window has a Basic properties panel at top.
- Enter the following:
- Name: name your credential
- Description: enter a useful description for the credential
- Enter your credentials data according to which credential category you are working with. Credential categories are discussed below, per category.
User/Password Credentials
This credential only defines a user/password pair (without a domain). It can be reused in other credential categories.
Enter the following:
- User: enter a user name.
- Password: enter the user name’s password
- Repeat Password: enter that user name’s password again
Click Accept to save the credential.
Authenticated User/Password Credentials
The credentials you create here allow the use of authenticated user/password pairs in the automatic creation of monitors. You should use an Administrator’s name in order to be able to capture the most devices.
Enter the following:
- Authentication Method: enter an authentication method. Select one of the following:
- *ANY
- *ANYSAFE
- Basic
- Digest
- GSS-Negotiate
- NTLM
- Select User/Password: select the user/password pair from the drop-down list box (these are the credentials you created in User/Password Credentials).
Click Accept to save the credential.
Database DSN Credentials
These are the user/password credentials used to connect to a database that you wish to be able to monitor.
Enter the following:
- DSN: enter the name of the DSN
- Select User/Password: select the user/password pair from the drop-down list box for the DSN. Please see User/Password Credentials for information regarding creating user/password pairs.
Click Accept to save the credential.
FTP Credentials
These credentials will create monitors automatically for FTP servers on the networks you specify.
Enter the following:
- Port: enter the TCP port number that the FTP is using (21, by default)
- Select User/Password: select a user/password pair from the drop-down list box (these are the credentials you created in User/Password Credentials).
Click Accept to save the credential.
iSeries Credentials
These credentials will create monitors automatically for FTP servers on the networks you specify.
Enter the following:
- Port: enter the TCP port number that the FTP is using (8082 by default)
- JiSS server: enter the name of the server where the IBMi is located (LOCALHOST by default)
- Select User/Password: select a user/password pair from the drop-down list box (these are the credentials you created in User/Password Credentials).
Click Accept to save the credential.
JMX Digital Certificate Credentials
The credentials you create here will create monitors for programs that use JMX.
Enter the following:
- Protocol: enter the protocol by which your JMX server uses, like JMXMP, RMI, or SOAP
- Service Name: enter the name of the WAS service running on the server
- Port: enter the port number that the WAS service uses on the JMX server (8081, by default)
- Trust Store File: enter the truststore file that contains the public keys for target servers
- Trust Store Password: enter the password for the truststore file
- Repeat password: re-enter the password for the truststore file
- Trust Key Store: enter the key store file that contains both public keys and private keys
- Trust Key Store Password: enter the password for the keystore file
- Repeat password: re-enter the password for the keystore file
- Host where JMX Service is located: enter the name of the machine where this ThinkServer component is located
- Port where the JMX Service is listening: enter the port where this ThinkServer component is listening
- Select User/Password: select a user and password pair from the drop-down list box
Click Accept to save the credential.
Microsoft 365 Credentials
This credential is defined by the Tenant ID ( of the Microsoft 365 subscription), the Client ID and its secret key created in Microsoft 365 to allow API access.
Enter the following:
-
Tenant ID: enter the Id of the Microsoft 365 subscription to which this credential will be applied.
-
Client ID: enter the client id needed to access this subscription.
-
Client secret key: enter the secret key that was generated for the client ID
-
Repeat client secret key: re-enter the secret key
Click Accept to save the credential.
Oracle TNS Credentials
These are the user/password credentials used to connect to an Oracle database that you wish to monitor.
Enter the following:
- TNS: enter the name of the TNS
- Select User/Password: select the user/password pair from the drop-down list box for the TNS. Please see User/Password Credentials for information regarding creating user/password pairs.
Click Accept to save the credential.
POP3 Credentials
The credentials you create here will be used to connect to POP3 servers.
Enter the following:
- Port: enter the port in use by your POP3 server (110, by default)
- Authentication Method: enter the type of authentication used by the server. Select from:
- None
- SSL
- Select User/Password: select the user / password pair from the drop-down list box. Please see User/Password Credentials for information regarding creating user/password pairs.
Click Accept to save the Credential.
Proxy Credentials
The credentials you create here will be used to determine the user/password pair, authentication method and a type, host and port for the Proxy.
-
Type: select the type of connection to be made to the proxy. Select from:
-
HTTP
-
HTTPS
-
SOCKS4
-
SOCKS5
-
-
Host provider: enter the name of host provider of the proxy
-
Port: Enter the port number on which to connect to the proxy. The default setting is 443.
-
Authentication method: select the authentication method to be used. Select from:
-
None
-
SSL
-
TLS/STARTTLS
-
-
Select user/password: Use the drop-dwon menu to select the user/password pair to be used to access the proxy.
Click Accept to save the Credential.
SMTP Credentials
The credentials you create here will create monitors for mail servers.
Enter the following:
- Port: enter the port in use by your SMTP server (25, by default)
- Authentication Method: enter the type of authentication used by the server. Select from:
- None
- SSL
- TLS/STARTTLS
- Select User/Password: select the user / password pair from the drop-down list box. Please see User/Password Credentials for information regarding creating user/password pairs.
Click Accept to save the credential.
SNMP v1/v2 Credentials
The credentials you create here will create monitors for hardware and software using SNMP versions 1 and 2.
Enter the following:
- Port: enter the remote port listening via SNMP (161, by default)
- Community: Enter the name of the community used for SNMP read access to the defined device.
Click Accept to save the credential.
SNMP v3 Credentials
The credentials you create here will create monitors for hardware and software using SNMP versions 3.
Enter the following:
- Port: enter the remote port listening via SNMP (161, by default)
- Authentication Protocol: enter the protocol used to encrypt the authentication with the client. Enter one of the following:
- None: no encryption used. Operates in the same way as SNMP v1 and v2.
- MD5: an authentication passphrase is entered and MD5 hashed. The MD5-hashed passphrase is used to access the target system.
- Authentication PassPhrase: enter the passphrase (key) which will be used to encrypt the credentials (only if you have chosen an authentication protocol).
- Repeat Passphrase: re-enter the passphrase
- Privacy Protocol: enter the protocol used to encrypt data retrieved from the target (only if you have chosen an authentication protocol, you cannot have privacy without authentication). Enter one of the following:
- None: if no data encryption is used. Operates in the same way as SNMP v1 and v2.
- DES: if SNMP v3 uses a privacy key to encrypt data using the DES algorithm.
- AES CFB128: if it uses a privacy key to encrypt data using the AES algorithm.
- Privacy Key: enter the passphrase (key) which will be used to encrypt the data (only if you have chosen an authentication protocol).
- Repeat Privacy Key: re-enter the passphrase
- Security Level: enter the security level selected using the authentication and privacy protocols. Enter one of the following:
- NoAuthNoPriv: no authentication and no privacy.
- AuthNoPriv: authentication, no privacy.
- AuthPriv: authentication and privacy.
- Security Name: enter the security name.
Click Accept to save the credential.
SSH (Public Key) Credentials
The credentials you create here will create monitors automatically for applications using public key-SSH.
Enter the following:
- Port: enter the port where the SSH server is listening (22 by default)
- PKI file: enter the Entrust public key infrastructure (PKI) file name
Click Accept to save the credential.
SSH (User/Password) Credentials
The credentials you create here will create monitors automatically for applications using user/password-SSH.
Enter the following:
- Port: enter the port where the SSH server is listening (22 by default)
- Select User/Password: select the user / password pair from the drop-down list box. Please see section User/Password Credentials for information regarding creating user/password pairs.
Click Accept to save the credential.
Telnet (User/Password) Credentials
The credentials you create here will create monitors automatically for systems using Telnet.
Enter the following:
- Port: enter the port where the Telnet service is listening (21 by default)
- Select User/Password: select the user/password pair from the drop-down list box. Please see User/Password Credentials for information regarding creating user / password pairs.
Click Accept to save the credential.
WebSphere MQ Credentials
The credentials you create here will create monitors automatically for systems using WebSphere MQ.
Enter the following:
- Port: enter the port number that the Queue Manager uses on the server (1404, by default).
- Queue Manager Name: the name of the Queue Manager you wish to monitor: localhost, by default.
- SVRCONN Name: the name of the server connection used by the Queue Manager.
- MCA User ID: enter the user identifier string that will be used by the Message Channel Agent.
Click Accept to save the credential.
Windows Domain User Credentials
The credentials you create here will create monitors automatically for the domains you specify.
Enter the following:
- Domain: enter the name of the Windows domain you wish to monitor.
- User: enter the name of a Windows user on that domain. Note: use an Administrator’s credentials here to be able to target more infrastructure.
- Password: enter the password for the Windows user on that domain.
- Repeat password: re-enter the password for the Windows user on that domain.
Click Accept to save the credential.
