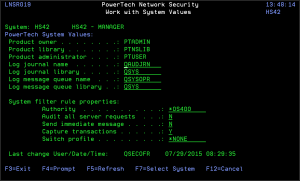
Work with System Values allows you to maintain system values for Powertech Network Security. The system values for Log Journal Name, Log Journal Library, Log Message Queue Name, and Log Message Queue Library can be maintained anytime. Values for Product Owner, Product Library, and Product Administrator can only be maintained during installation or upgrade.
On the browser interface, these values can be found at Edit System Defaults.
How to get there
To display these options, from the Network Security Main Menu, select option 81, Configuration Menu, then option 1, Work with System Values.
Field Descriptions
The following describes the parameters and allowable values for each field on the Work with System Values panel.
Product Owner
The product owner is the name of the user profile that owns all data objects and exit programs in the Powertech Network Security product.
Product Library
The product library is the library that contains all of the Powertech Network Security objects.
Product Administrator
The product administrator is the name of the user profile that owns administrative program objects in the Powertech Network Security product. We recommend granting administrators *USE authority to the PTADMIN authorization list using the following command, where myuser is the administrator profile to add.
ADDAUTLE AUTL(PTADMIN) USER(myuser) AUT(*USE)
For more information, see Granting Reporting Authority, later in this User Guide.
Once authorized to the PTADMIN and PTNSRPT authorization lists, the administrator has all the authorities needed to administer Powertech Network Security. Product administrators have *CHANGE authority to Network Security data and *USE authority to Network Security programs.
Log Journal Name and Log Journal Library
The log journal name is the name of the journal that Powertech Network Security will log information. You can control the level of detail with the audit flag when you specify location and user authorities. Most installations will specify QUADJRN. The log journal library specifies the library where the log journal is located.
The Log Journal Library specifies the library where the log journal is located.
- You also can specify *NONE in the Log Journal Name field. However, if a journal name of *NONE is found in the Network Security system values, network transactions are not journaled.
- Some versions of Powertech Compliance Monitor expect Network Security audit entries to be written to QSYS/QAUDJRN. Contact Powertech technical support if you need further information concerning log journal entries.
Log Message Queue Name and Log Message Queue Library
The log message queue name is the name of the message queue where Powertech Network Security sends messages. Messages are sent to this queue when specified on location and user authority records. Most installations specify QSYSOPR.
The log message queue library is the library where the log message queue is located.
System Filter Rule Properties
The Work with System Values panel also allows you to specify system filter rule properties.
Authority
The authority assigned if no other authority is found for a server or function. Possible values are:
Audit All Server Requests
Controls the type of requests Network Security will log. Network Security uses this value if no other value is entered for a server or function. Possible values are:
Send Immediate Message
Determines if Network Security sends a message to the log message queue. Network Security uses this value if no other value is entered for a server or function. Possible values are:
Capture Transactions
Capture transactions for Memorized Transaction Request (MTR). Network Security uses this value if no other value is entered for a server or function. Possible values are:
Switch Profile
The name of a Switch Profile. If you enter a profile name, processing is switched to run as the specified profile and under this profile's authority. Network Security uses this value if no other value is entered for a server or function. Possible values are:
Last Change User/Date/Time
The user profile that changed the Network Security system values and the date and time the changes were made.
Command Keys
F3 (Exit): Exit the current panel without processing any pending changes.
F4 (Prompt): Displays a list of possible values from which you may select one.
F5 (Refresh): Refreshes the panel and resets all available text fields.
F7 (Select system): Use this command to work with data from a different System.
F12 (Cancel): Exit the current panel without processing any pending changes.